This commentary was provided by Tom Makau (tom.makau@ebiashara.com), Head of Infrastructure and Security at eBiashara Africa Ltd who is a member of the Association. Tom presented on the subject at the Regional Members’ Meeting in Nairobi on 6th September 2023.
CYBER SECURITY RISK
WHAT YOU CAN DO ABOUT IT
This commentary was provided by Tom Makau (tom.makau@ebiashara.com), Head of Infrastructure and Security at eBiashara Africa Ltd who is a member of the Association. Tom presented on the subject at the Regional Members’ Meeting in Nairobi on 6th September 2023.
Introduction
Were it an economy, proceeds from Cybercrime activities would be the third largest after the US and China. Cybercriminals have evolved from curious tinkering teens into organized armies of hackers for hire by governments and the private sector. A good example is the Lazarus Group that was hired by the North Korean Government to attempt steal over USD 1 billion from the Society for Worldwide Interbank Financial Telecommunication (SWIFT) system used by financial institutions globally. This was detected and stopped but not before the Bank of Bangladesh lost USD 81 million and Cosmos Bank in India USD 13.5 million.
The main motivation for cybercrime remains money. Directly hacking financial systems such as the SWIFT network and targeting financial institutions’ IT systems is the de facto method of cyber theft of money. The Lazarus Group is said to have stolen over USD 2 billion to date in cash and cryptocurrency.
Unlike money that is single use, once you spend it its gone, data can be reused and combined in different ways to yield new information. The second motivation for cybercriminals is to steal data or hold data at ransom for a payout. Money from data can be extracted through extortion, learning of business secrets, ransom etc. Data can also be used for non-monetary gains such as settling personal or national scores and national or military espionage.
How they get in
There are several ways through which cybercriminals can gain entry into your information systems and tools. Worth noting however, is that research by Deloitte, found that 91% of all cyberattacks begin with a phishing email (an email that looks like it’s from someone you know but is actually from criminals). This email will have a call to action to click on a link or share information with them as you believe them to be genuine people. Other ways in which they can gain access is through compromised passwords that were either deliberately or inadvertently shared or found their way into criminal hands. Weak passwords also come close to compromised passwords with a 2022 survey in the US showing that over 33% of Americans use their pet names as passwords for critical systems and communication.
We have been witnessing an increase in hijacking of internet connected devices by cybercriminals to use them as part of botnets: a network of compromised devices that can be used to simultaneously generate copious amounts of traffic targeting a service or network. This is known as a Distributed Denial of Service (DDoS) attack. We have unknowingly enabled the increased frequency and power of DDoS attacks through failure to change default passwords on connected devices such as security cameras, Wi-Fi (wireless) access points, and other IT equipment. The recent downtime in Kenya where the Minister for ICT and the Digital Economy confirmed that the eCitizen portal, M-PESA, and several banking platforms went down at the same time was as a result of a suspected DDoS attack. Changing default passwords and using strong passwords denies these online hacker armies one more tool to use in their attacks.
Data and ransomware
Data and the resultant information from it, is increasingly becoming central to many businesses today. Without it, many businesses would grind to a halt. By gaining access into your IT systems, cybercriminals can prevent you from accessing and using data in your business through the use of ransomware. Ransomware works by encrypting all your data, making it inaccessible for general use unless you pay a specified ransom often in cryptocurrency such as Bitcoin. Recently a Kenyan retail business was affected by ransomware and their failure to pay the ransom saw their data that included internal office communication, customer communication and personal details shared online by the hackers.
Ransomware type of attacks are becoming the predominant way through which cybercriminals make money from data. This is aided by the proliferation of tools and hackers for hire to conduct them. It is also the approach with the highest ROI to hackers because many organizations value their data and its loss is an existential threat and would pay anything to regain access. Recently a ransomware attack at a Nordic data centre led to the wiping out of all the data centres. Customers’ data spanning many years of emails, business records, ERP databases, and software platforms all disappeared.
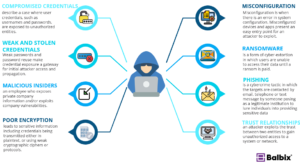
Closer to home, one of the EAA members lost about US$9,000 when his customer received a Phishing email ostensibly from the EAA member’s accountant about an offer to accept partial payment of USD 9,000 for a long outstanding USD 40,000 debt. This money was deposited into the cybercriminal’s bank account by the customer believing the EAA member to be Godsent for extending such favourable payment terms. Sometimes, cybercriminal activity is not indicated by red blinking computer systems, LED lights, and downward scrolling matrix movie alphabet on a computer screen and sirens depicted in Hollywood movies, but via a delightful thank you note email from your customer!
What do you need to do to secure your information assets and tools against cyber-attacks?
- Start Today
Create a dedicated cross functional team to identify critical information assets to be protected. This team will be responsible for creating and updating cybersecurity policies and procedures. A good starting point is conducting a Vulnerability and Penetration Testing (VAPT) assessment on your IT systems and infrastructure. A VAPT will identify vulnerabilities in your systems and processes. For example, it can identify usernames in your systems that have a high level of privilege but have never used this in a long time. It can identify weaknesses in the network or computer operating systems that can be exploited by criminals. It can also identify malicious and unusual activity patterns such as the midnight transfer of a large number of files from your IT systems to an external destination or an employee VPN connection from a country different from where you expected them to be etc.
- Automate
Cybercriminals are always trying to be a step ahead of measures and techniques to stop them. As a result, the rapid change in tactics and tools, means that it will be nearly impossible to remain secure for long if you are not also constantly modifying your security measures to adapt to new threats. Automation enables compliance to, and enforcement of, cybersecurity policies. For example, a rule to not bring in and use USB memory sticks can easily be enforced through ensuring that all company computers have their USB ports disabled to read memory sticks, this removes the decision away from the user to the system.
- Follow best practice
Simple best practices such as the use of Multi Factor Authentication (MFA), can lower the success of automated attacks by up to 99.9% and the chances of a ransomware attack by up to 80%. MFA is the equivalent of the discovery of vaccines in the medical world. A simple yet powerful way to keep hackers at bay. The recent Executive Order on Federal cybersecurity by US President Biden, had five pillars of ensuring security of federal IT systems, MFA was one of them.
Another best practice is the adoption of a Zero Trust Policy where users of IT systems are by default not trusted and are given access/trust on a need and case basis. For example, in many IT organizations, there is always an administrator user account with all the rights and privileges on the system. The system administrator was its God and anyone with this level of access could potentially cause damage if they so wished. In a Zero Trust environment, these privileges are given only to users based on their role and context. This limits the chances of cybercriminals’ effectiveness in instances where they succeed in gaining entry as they will not find a single user with all the rights and permissions to carry out their activities in time or successfully.
- Secure the supply chain
Cybercriminals might still gain access into your systems despite you throwing top dollar and talent at securing them. This can be done through one of your IT suppliers in what is known as a supply chain attack. It is important to ensure that other than securing your systems, your suppliers also do the same. The SolarWinds Supply chain attack is an example of how a foreign entity gained access to the US Government’s top-secret networks and systems after several US Government bodies, including the Pentagon, did a routing update on their SolarWinds software tool and in the process brought in malicious code that gave cybercriminals unfettered access to data and classified information for close to a year. A cybercriminal who wants to target a financial institution will find a plethora of defences at the bank, but none, if any, at one of their IT suppliers. This will be their point of entry. This is the Trojan horse of the cybercrime world.
Conclusion
With cybersecurity increasingly becoming a major risk to most organizations, there is no business that is too small or insignificant to be hit by cybercrime. The existential risk posed by loss of data or access to systems containing this data means that this risk is no longer something that IT handles, but now requires the involvement of senior management and business owners in addressing the potential outcomes of falling victim. Government regulations such as the Data Protection Act also impose fines to organizations that fail to ensure data privacy or disclose data breaches due to process failure or cybercrime. Such a law makes it even more important that you start today.
Please speak to us at eBiashara Africa Ltd on how we can work with you to protect your information assets and tools.
